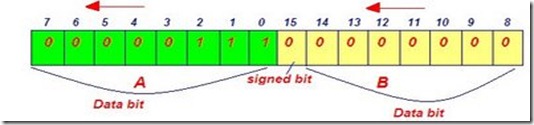
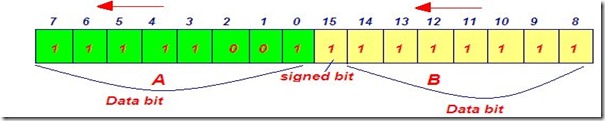
 |
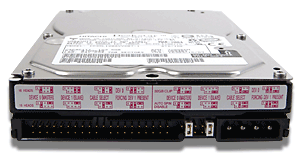
| IDE HDD |
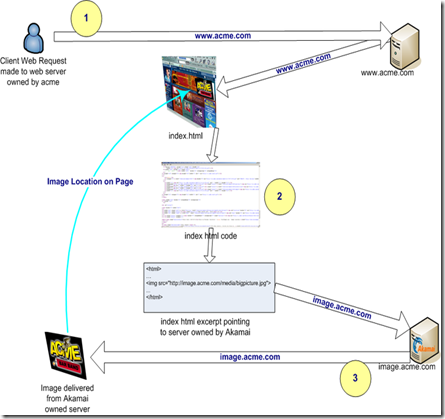
SATA (Serial Advanced Technology Attachment)– a 1-bit serial evolution of the Parallel ATA physical storage interface.
Starting with SATA, it extends the capabilities of ATA and offers transfer rates starting at 150MB/s and, after years of development, has moved to the mainstream of disk interfaces. The successor the SCSI interface is SAS at speeds of up to 3Gb/s. Additionally, it also addresses parallel interface issues such as drive addressability and limitations on the number of device per port connection.
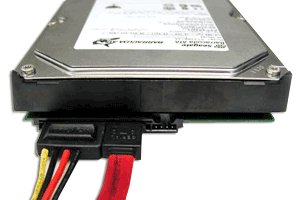 |
| SATA |
SCSI
Short for small computer system interface, a parallel interface standard used by Apple Macintosh computers, PCs and many UNIX systems for attaching peripheral devices to computers. Nearly all Apple Macintosh computers, excluding only the earliest Macs and the recent iMac, come with a SCSI port for attaching devices such as disk drives and printers. SCSI interfaces provide for data transmission rates (up to 80 megabytes per second). In addition, you can attach multiple devices to a single SCSI port, so that SCSI is really an I/O bus rather than simply an interface.
Cables & Connectors:Another big advantage of SATA over ATA is the cabling and connectors. The serial interface reduces the amount of wires needed to transmit data, making for much smaller cable size and making it easier to route and install SATA devices. The IDE cables used in parallel ATA systems are bulkier than Serial ATA cables and can only extend to 40cm long, while Serial ATA cables can extend up to one meter. In addition to the cabling, a new design of connectors is also used that reduces the amount of crosstalk between the wires, and the connector design also provides easier routing and better air flow.
 |
| 26-inch Internal SCSI Cable |
 |
| External SCSI4 Cable |
 |
| SATA Internal Power Splitter Cable |
 |
| Serial ATA Drive Connection Cable |